How to create optimized identity lifecycle management process to secure finance enterprises

Getting identity lifecycle management right is more important than ever. As companies pivot to remote work and embrace digital transformation, they face the tricky task of ensuring security while keeping things user-friendly. This article explores the nuances of managing user identities and how to create a secure yet smooth user experience through effective identity and access management solutions.
Steering through the digital shift
With digital transformation speeding up and remote work becoming the norm, how organizations handle identity-related processes is changing. Picture a busy airport where travelers (users) need to quickly pass through security checks (authentication) to catch their flights (access to resources). Just like airports aim to keep security tight without causing delays, businesses need to strike a balance between strong security measures and user convenience through efficient identity management strategies.
Balancing security and user ease
In this digital age, security and productivity are like two sides of the same coin. Companies must ensure their identity management processes are both secure and user-friendly. It’s like a tightrope walker maintaining balance to avoid a fall. Focusing too much on security can make processes cumbersome, while prioritizing ease of use could open up vulnerabilities, increasing security risks.
Transforming identity management with automation
Automation is the powerhouse behind the evolution of identity handling. Think of it as the autopilot in a plane, efficiently handling routine tasks like user onboarding and offboarding, which are crucial stages of lifecycle management. By automating these processes, companies can cut down on errors, boost efficiency, and allow IT teams to focus on more strategic tasks, optimizing the identity lifecycle.
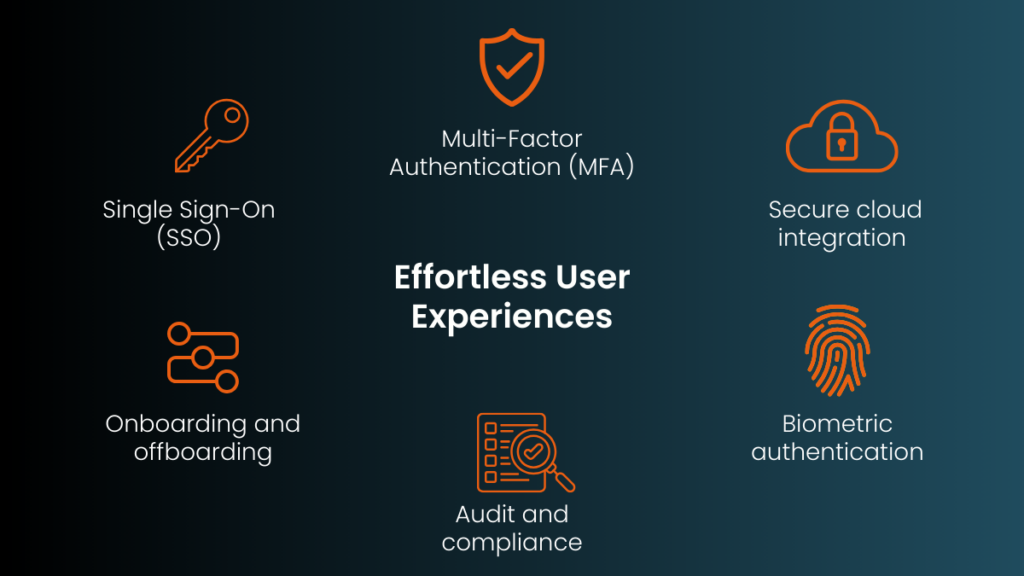
Moving towards effortless user experiences
The demand for secure, seamless user experiences is on the rise in our digital-first world. As remote work becomes standard, the need for optimized identity processes grows. This shift is similar to how smartphones have become essential by integrating multiple functions into one device, much like modern identity management solutions integrate various identity processes.
Remote work’s impact on identity management
Remote work has turned the traditional office into a virtual space, requiring robust identity solutions. It’s like moving from a single-family home to a high-rise apartment, where access control and security need rethinking to accommodate a larger, more varied group. This involves managing identities and ensuring access to systems and applications is secure.
Integrating identity management with business apps
Merging identity management with business apps is key for creating scalable workflows. Imagine it as a symphony orchestra, where each instrument (application) must play in harmony to create a cohesive performance. Solutions like Keycloak can help achieve this harmony, boosting both security and productivity by ensuring access permissions are correctly assigned.
In summary, navigating the new digital landscape requires a strategic approach to managing user identities. By embracing automation, balancing security with user convenience, and integrating identity management with business apps, organizations can deliver a seamless user experience that meets today’s digital demands.
Tools for streamlined identity management
As digital landscapes evolve, optimized identity processes are becoming a cornerstone for organizations aiming to balance security and productivity. With remote work and digital transformation reshaping operations, efficient identity management is more crucial than ever. Let’s explore the essential features and capabilities for achieving this optimization, including identity governance and compliance.
Automating identity processes for efficiency
A major advancement in identity management is moving from manual to automated processes. Automation is key in streamlining user onboarding and offboarding, vital parts of account lifecycle management. By automating these tasks, companies can significantly reduce errors and boost efficiency, ensuring users have the right access at the right time, thereby preventing unauthorized access.
Automated access management not only enhances efficiency but also strengthens security by reducing human error, a common source of vulnerabilities. This shift towards automation is crucial for optimized identity processes, enabling organizations to handle user identities more effectively and securely, ensuring compliance with governance standards.
Enhancing business workflows through integration
Another vital feature of optimized identity management is integration with business applications. By linking identity management solutions with business applications, companies ensure identity processes are efficient and aligned with business goals, optimizing identity lifecycle management.
This integration boosts both security and productivity by providing a unified approach to managing user identities across various platforms. It offers a more cohesive and streamlined user experience, essential in today’s digital-first world. As businesses adopt more applications and services, the ability to integrate identity management with these tools becomes increasingly important, enhancing identity governance.
Adapting to the new norm
Balancing security and productivity in identity management
In the quest for optimized identity processes, organizations face the challenge of balancing security with user convenience. Implementing solutions like Single Sign-On (SSO) and Multi-Factor Authentication (MFA) can help achieve this balance. These tools mitigate security risks while maintaining a seamless user experience, ensuring security measures don’t hinder productivity.
Ensuring compliance through effective data management
Effective data management is another critical aspect of optimized identity processes. Establishing a single, reliable source of truth for user data across platforms is essential for data integrity and compliance. Continuous monitoring and audit readiness are crucial for meeting regulatory requirements and safeguarding sensitive information, ensuring access to sensitive data is controlled.
By focusing on these features and capabilities, organizations can adapt to the new norm of remote work and digital transformation, achieving a secure and productive environment through optimized identity management.
Achieving lifecycle maturity
In today’s fast-evolving digital landscape, reaching lifecycle maturity in identity management is not just a goal but a necessity. As organizations strive to balance security and productivity, the journey towards optimized identity processes becomes crucial. This section explores strategies and tools to guide organizations towards this promised land, including role-based access control and privileged access management.
Gradual modernization for mastering identity processes
Optimized identity management is a journey, not a destination. The path to lifecycle maturity involves gradual modernization, where incremental improvements are key. By adopting a phased approach, organizations can capture early wins and see a return on investment (ROI) sooner. This strategy allows for identifying and resolving potential issues early, ensuring a smoother transition to fully optimized identity processes.
Gradual modernization involves shifting from manual to automated processes, enhancing efficiency and reducing errors. By automating user onboarding and offboarding, organizations can streamline operations and improve security, ensuring access rights are properly managed. This approach not only boosts productivity but also ensures consistent application of security measures.
Building a unified directory with lifecycle awareness
A unified directory with lifecycle awareness is a cornerstone of optimized identity management. Centralized management of user identities enhances visibility and control, enabling organizations to manage access rights and permissions more effectively. This centralized approach ensures user data is consistent and reliable across all platforms, creating a single source of truth.
Universal directories are crucial in storing and managing identity data. They provide a comprehensive view of user identities, allowing organizations to make informed decisions about access management. By integrating identity management with business applications, organizations can ensure workflows are seamless and scalable, further enhancing both security and productivity.
Conclusion
In conclusion, achieving lifecycle maturity in identity management is essential for organizations navigating today’s digital landscape. By embracing gradual modernization and implementing a unified directory with lifecycle awareness, organizations can optimize their identity management processes. This approach not only balances security with productivity but also ensures compliance and effective data management.
- Embrace automation for efficiency: Transition from manual to automated processes to streamline operations and enhance security.
- Integrate identity management with business applications: Ensure seamless, scalable workflows that enhance both security and productivity.
- Balance security with user convenience: Implement solutions like Single Sign-On and Multi-Factor Authentication to reduce security risks while maintaining user convenience.
- Ensure compliance and data management: Create a single, reliable source of truth for user data and maintain continuous monitoring and audit readiness.
By following these strategies, organizations can achieve a seamless user experience and thrive in the digital-first world, leveraging identity management tools and solutions to manage access and identity profiles effectively.
Interested in IAM solutions? Schedule a call with our expert
Fill out the form and let our experts contact you to start your authentication journey.