The ultimate guide to customer identity management lifecycle – key stages

Customer identity management lifecycle (CIAM lifecycle) isn’t just a behind-the-scenes IT task—it’s a strategic cornerstone for businesses. As companies dive into digital transformation, mastering this process is key. Let’s walk through the essential steps to effectively manage customer identities and access rights.
Navigating the identity and access management landscape
Picture a lively city where everyone needs a unique ID card to access services like public transport and healthcare. That’s similar to how digital access works in the online realm, where we issue and manage digital ID cards. The Customer Identity Management Lifecycle is the process that ensures these digital identities are created, verified, and managed securely throughout their entire lifecycle.
Understanding the identity lifecycle management process
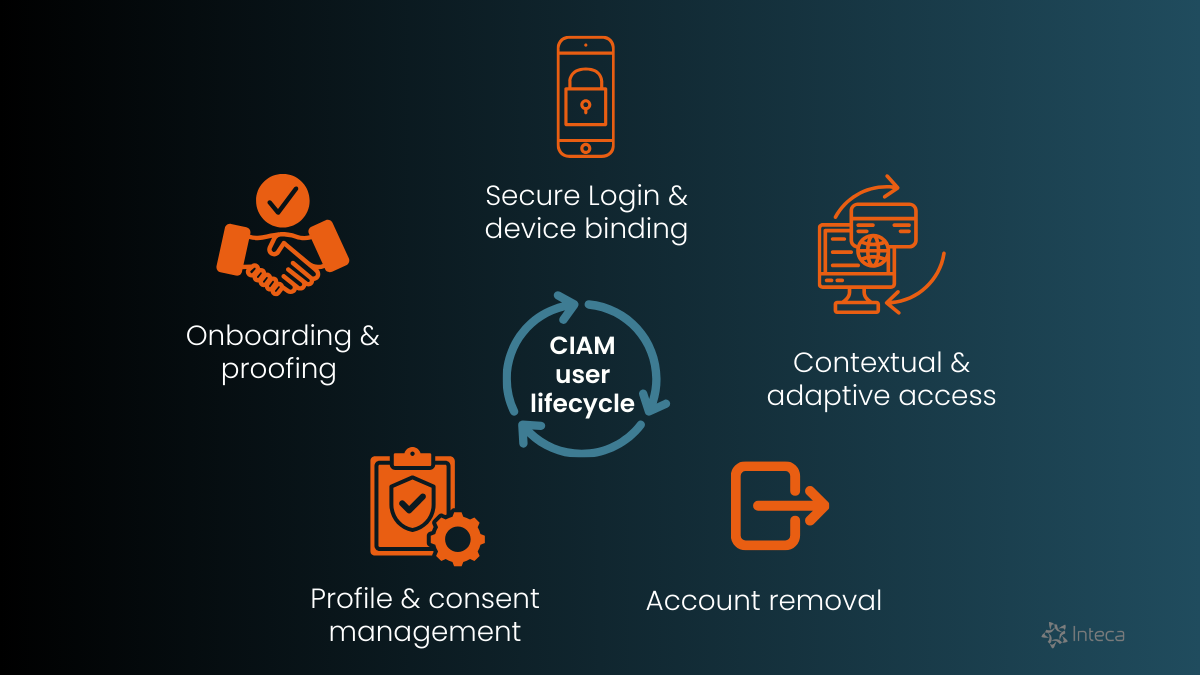
The CIAM lifecycle is a structured process of managing customer identities, covering stages like onboarding, identity proofing, secure login, device binding, contextual and adaptive access, profile management, consent management, data management, and account removal. Each step is crafted to boost security, enhance user experience, and meet regulatory standards. This process of managing identities and access ensures compliance and mitigates the risk of unauthorized access.
The importance of identity governance for businesses today
In a world where data breaches and identity theft are all too common, businesses must focus on managing user IDs and controlling access. A solid CIAM lifecycle not only shields sensitive data but also builds trust and loyalty. It empowers businesses to offer personalized experiences while protecting user privacy and ensuring that access to resources is granted appropriately.
Key steps in the customer identity management lifecycle process
The CIAM lifecycle is a journey starting with onboarding and concluding with account removal. Each step is interconnected, forming a seamless process that ensures secure and efficient identity management. Here’s a quick rundown:
- Onboarding – introducing customers to the system and managing user provisioning.
- Proofing – verifying customer identities through identity verification.
- Secure login – implementing strong login methods and password management.
- Device binding – linking devices to user identities for extra security.
- Contextual & adaptive access – tailoring access based on user context and access control policies.
- Profile management – managing user profiles for personalized experiences.
- Consent management – handling user consent to build trust.
- Data management – ensuring secure data handling and managing customer data.
- Account removal – safely deactivating accounts when needed, automating the offboarding process.
Step 1: onboarding
These initial phases are crucial for establishing trust and ensuring a seamless user experience, which are essential for effective management of user IDs and access permissions. Onboarding is the gateway to managing customer access. A smooth onboarding process is key for making a good first impression and ensuring users can easily access services without unnecessary friction. In the CIAM lifecycle, onboarding isn’t just about gathering user information; it’s about creating a welcoming and efficient entry point that enhances user satisfaction and loyalty.
Features and capabilities – how technology facilitates efficient onboarding
Modern technology is pivotal in streamlining onboarding. Automated workflows, intuitive interfaces, and real-time data validation are some features that make onboarding efficient. By leveraging these capabilities, businesses can reduce drop-off rates and improve user engagement, setting a strong foundation for the CIAM lifecycle. User provisioning and deprovisioning are crucial components of this process.
Step 2: proofing
Proofing verifies a user’s identity to ensure they are who they claim to be. This step is critical in the CIAM lifecycle as it builds the trust necessary for secure interactions. Effective identity proofing is a cornerstone of managing user IDs, helping to prevent fraud and unauthorized access.
Features and capabilities – tools for effective identity proofing
To achieve robust identity proofing, businesses can use tools like biometric verification, document scanning, and multi-factor authentication. These solutions enhance the accuracy and reliability of identity proofing, strengthening strategies to ensure only verified users gain access to sensitive information.
Step 3: secure login
Secure login mechanisms are fundamental to safeguarding user data and maintaining the integrity of managing user IDs. By implementing strong authentication protocols, businesses can prevent unauthorized access and protect sensitive information from cyber threats. Secure login is a crucial part of the CIAM lifecycle, reinforcing the security of digital interactions.
Features and capabilities – implementing robust login mechanisms
To enhance secure login, organizations can deploy technologies like single sign-on (SSO), two-factor authentication (2FA), and passwordless authentication. These features not only improve security but also enhance user experience by simplifying the login process. By adopting these capabilities, businesses can balance security and convenience, a key goal of the CIAM lifecycle.
Step 4: device binding
Device binding links user identities to specific devices, adding an extra layer of security to customer access. This step is crucial in the CIAM lifecycle as it ensures only authorized devices can access user accounts, reducing the risk of unauthorized access.
Features and capabilities – technology solutions for device binding
Advanced technology solutions like device fingerprinting and secure token storage enable effective device binding. These capabilities allow businesses to monitor and manage device access, ensuring user data remains secure across platforms. By integrating device binding into their strategies, organizations enhance overall security.
Onboarding, proofing, secure login, and device binding are critical steps in the Customer Identity Management Lifecycle. By effectively implementing these processes, businesses can achieve robust customer access management, ensuring secure and seamless user interactions.
Step 5: contextual & adaptive access
Static access controls are outdated. The need for contextual and adaptive access is critical, allowing businesses to tailor access permissions based on user context. This approach enhances security and improves the user experience by providing seamless access to resources.
Features and capabilities – dynamic access management solutions
Dynamic access management solutions lead this transformation. These technologies enable businesses to implement adaptive policies considering factors like location, device, and user behavior. By leveraging these solutions, organizations ensure access is granted appropriately, reducing unauthorized access risk and enhancing security.
Step 6: profile management
Effective profile management is a cornerstone of the CIAM lifecycle. By managing user profiles efficiently, businesses can deliver personalized experiences meeting each customer’s unique needs, fostering loyalty and driving engagement and satisfaction.
Features and capabilities – tools for effective profile management
To achieve successful profile management, businesses must use advanced tools for seamless integration and management of user data. These tools provide insights into user preferences and behaviors, allowing organizations to tailor their offerings and interactions. This creates a more personalized and engaging customer journey.
Integrating contextual and adaptive access and profile management within the Customer Identity Management Lifecycle is essential for modern businesses. By embracing these strategies, organizations enhance their capabilities, ensuring secure, efficient, and personalized interactions in the digital landscape.
Step 7: account removal
In managing customer identities, the final step in the Customer Identity Management Lifecycle (CIAM lifecycle) is account removal. This crucial phase ensures businesses handle deactivating user accounts securely and compliantly, maintaining trust and adhering to regulatory requirements.
Account removal isn’t just about deleting a user’s profile; it involves a comprehensive process ensuring all associated data is handled responsibly. This step is vital for maintaining the integrity of managing customer access and user IDs. By implementing robust strategies, businesses ensure account deactivation is secure and compliant with data protection regulations.
Features and capabilities – streamlining the account removal process
To manage account removal effectively, organizations must use advanced technologies that streamline the process. These solutions should offer features like automated workflows for account deactivation, secure data deletion protocols, and audit trails to ensure compliance. By integrating these capabilities into the CIAM lifecycle, businesses enhance their overall customer identity management strategy.
Embracing identity governance and administration
More businesses recognize managing customer access as a vital part of their digital strategy, driven by the need to enhance security, improve user experiences, and comply with evolving regulations. This involves managing access privileges and enforcing access control.
The increasing importance of identity governance and administration
As digital interactions become standard, managing customer access effectively is crucial. Businesses need to ensure only authorized users access their systems, safeguarding sensitive data from unauthorized access. This requires a robust framework that adapts to changing user behaviors and threats, incorporating role-based access control and regular access reviews.
How identity solutions are evolving in user ID management
The evolution of managing user IDs and access is marked by technologies like biometrics, multi-factor authentication, and AI-driven analytics. These innovations enable businesses to implement dynamic controls that adapt to user context, enhancing security without sacrificing user experience. Identity solutions are crucial in managing the entire lifecycle of digital identities within organizations.
Customer identity management lifecycle – challenges and opportunities
Businesses that effectively adapt to the CIAM lifecycle come out on top. They offer secure, seamless, and personalized experiences that boost customer satisfaction and loyalty. Conversely, businesses that neglect identity management risk losing customer trust and facing regulatory penalties. Effective identity lifecycle management becomes a competitive advantage.
The Customer Identity Management Lifecycle is crucial for businesses aiming to thrive in the digital era. By understanding and implementing each step effectively, organizations can ensure secure, efficient, and user-friendly identity management. Embracing the CIAM lifecycle is about achieving the goal of secure and seamless customer interactions.
Key Takeaways
The Customer Identity Management Lifecycle is vital for businesses using customers accounts. By understanding and implementing each step effectively, organizations ensure secure, efficient, and user-friendly identity management.
- Design the CIAM lifecycle to stay ahead in the digital landscape.
- Include technology to enhance each step of the process.
- Achieve the promised land of secure and seamless customer interactions.
By focusing on comprehensive management of customer access, user IDs, and control, businesses can build a robust CIAM lifecycle that protects sensitive data and fosters customer trust and loyalty. As digital transformation continues to evolve, the importance of a well-executed CIAM lifecycle cannot be overstated.
Take a first step to secure CIAM architecture
Fill out the form and let our experts contact you to start your customer authentication journey.






